Background
Nowadays, many Android apps implement encryption within shared object (so) files, making the reverse engineering of these files a time-consuming process. I have been contemplating whether there are any universal solutions. Based on online references, I have experimented with the following three approaches:
- Setting up an HTTP server on Android
- Establishing an HTTP server on Android along with using frp for intranet penetration
- Exposing an API using Sekiro
This article primarily focuses on the third method.
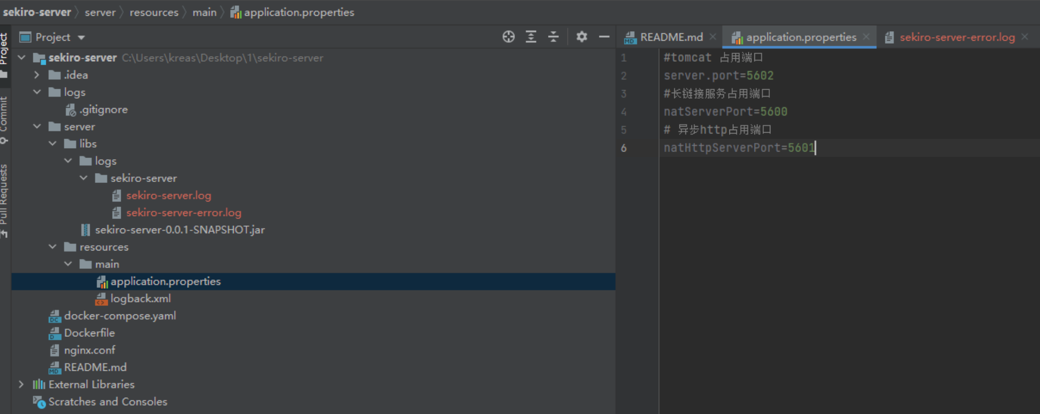
Configuration of Sekiro Server
Project link: https://gitee.com/maike1/sekiro.git This is a pre-packaged JAR file that can be used directly.
Writing the Xposed Module
- Import the Sekiro dependency package: Import the following in the dependencies tag of the app’s build.gradle file:
implementation 'com.virjar:sekiro-api:1.0.1' - Register within the
handleLoadPackagemethod under the xposed tag.
Log.i(TAG, "connect server....");
// 服务端host
String testHost = "192.168.0.106";
// 客户端标识
String clientId = UUID.randomUUID().toString();
// 接口组名称
String groupName = "addDemoTest2";
// 暴露的接口名称
String actionName = "myAdd";
// 拿classloader
final ClassLoader classLoader = lpparam.classLoader;
// 连接服务端并且注册处理的handler
SekiroClient.start(testHost, clientId, groupName)
.registerHandler(actionName, new SekiroRequestHandler(){
@Override
public void handleRequest(SekiroRequest sekiroRequest, SekiroResponse sekiroResponse){
//当服务端分配任务时, 这里处理逻辑, 并把结果返回给服务端, 服务端再返回给调用者
// Class<?> clz = XposedHelpers.findClass("com.example.administrator.adddemo.MainActivity", classLoader);
int arg1 = sekiroRequest.getInt("arg1");
int arg2 = sekiroRequest.getInt("arg2");
Log.i(TAG, String.format("arg1 : %d, arg2 : %d", arg1, arg2));
// Object result = XposedHelpers.callStaticMethod(clz, "Add", arg1, arg2);
String addNum = Integer.toString(arg1+arg2);
Log.i(TAG, "result : " + addNum);
sekiroResponse.success(addNum);
}
});
- Packaging and Compilation
TIP: If encountering a compilation error “More than one file was found with OS independent path”
- Solution: Add the following code under the android configuration in the build.gradle file to exclude some duplicate resources:
// Exclude duplicate files
packagingOptions {
exclude 'META-INF/*******'
exclude 'META-INF/INDEX.LIST'
exclude 'META-INF/io.netty.versions.properties'
}
Display of Invocation Results
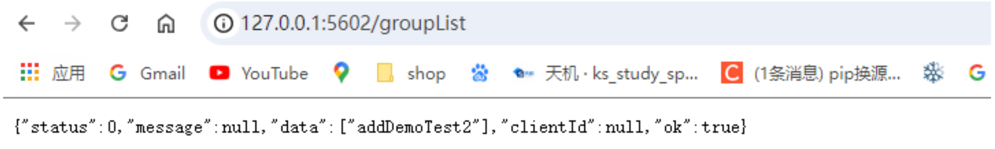
http://127.0.0.1:5602/groupList displays all groups registered in the current system
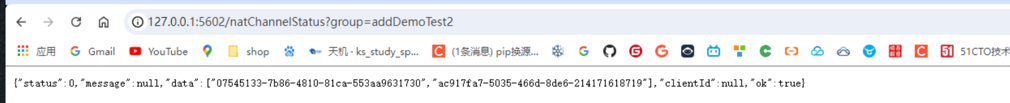
http://127.0.0.1:5602/natChannelStatus?group=addDemoTest2 displays the registered devices
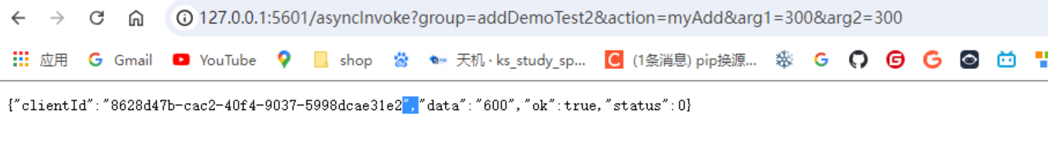
http://127.0.0.1:5601/asyncInvoke?group=addDemoTest2&action=myAdd&arg1=300&arg2=300 demonstrates the API invocation
This article is from: https://blog.csdn.net/m0_68075044/article/details/130172324